The work landscape is rapidly evolving, with a growing reliance on devices running iOS, Android, and ChromeOS across various form factors such as handhelds, tablets, pads, and Chromebooks. As organizations embraced remote work, mobile devices became the gateway to enterprise resources for many – housing corporate apps, authenticators and other credentials employees use to gain access to internal resources. In recent notable breaches, adversaries have targeted employees on mobile devices to harvest credentials or tokens to gain a foothold for a broader attack campaign. As mobile devices increasingly become integral to zero trust authentication and enterprise resource access, it is crucial to address their security needs.
Many organizations have turned to Mobile Device Management (MDM) solutions to tackle this challenge. However, MDM offers limited attack protection, focusing primarily on device management, configuration, and policy enforcement. MDM and MTD serve different yet complementary roles in ensuring mobile security. MDM focuses on managing devices and enforcing policies, while MTD is dedicated to detecting and mitigating threats targeting mobile devices.

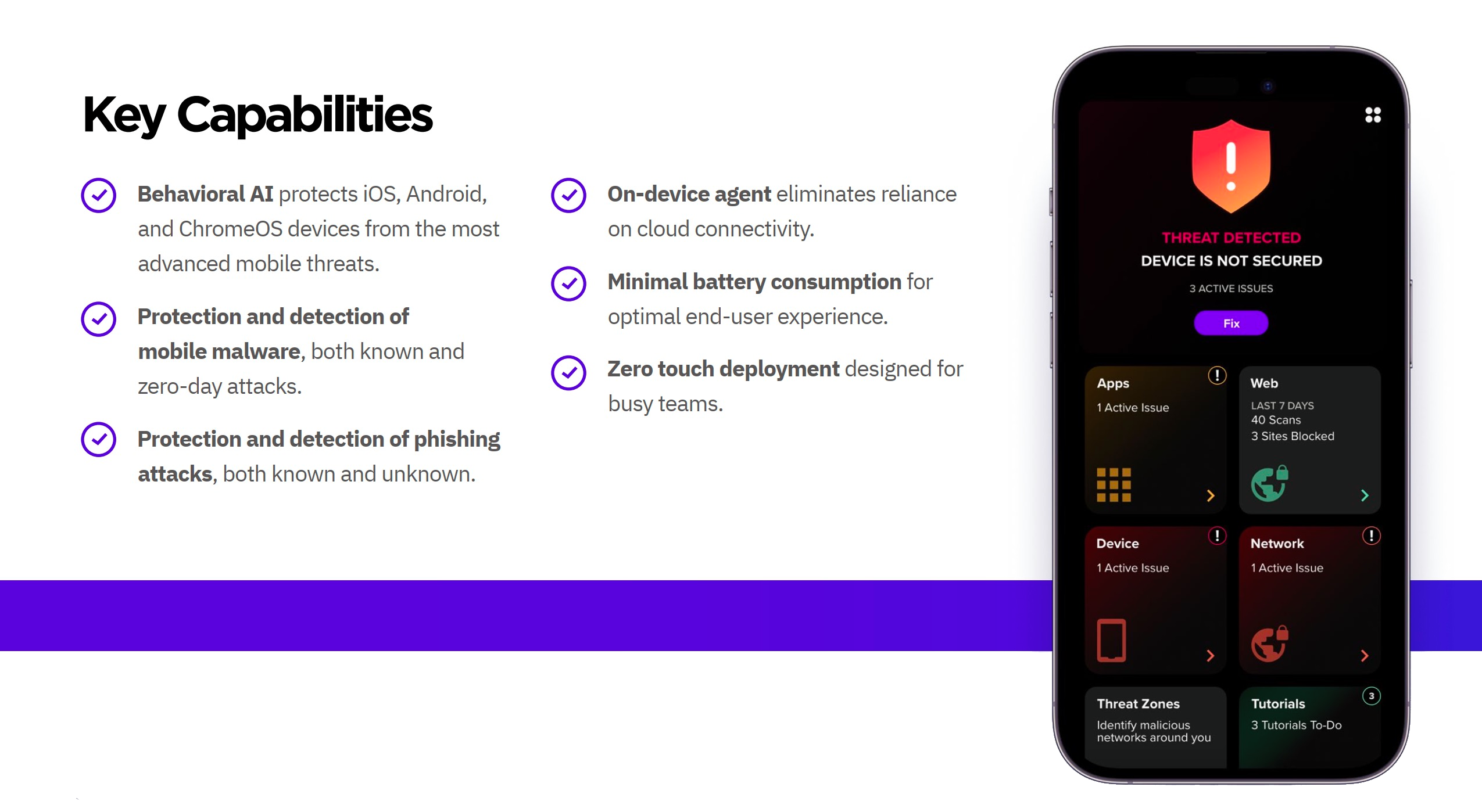
Ultimate Mobile, an AI-powered MTD solution, provides autonomous threat protection, detection, and response for iOS, Android, and ChromeOS devices. As an on-device behavioral AI product, it dynamically detects unprecedented malware, phishing, exploits, and man-in-the- middle (MiTM) attacks. Protecting mobile devices and users is critical, considering that the 2022 Verizon Mobile Security Index revealed that 45% of surveyed companies experienced a compromise involving a mobile device leading to data loss, downtime, or other negative outcomes.
Mobile Phishing & Smishing
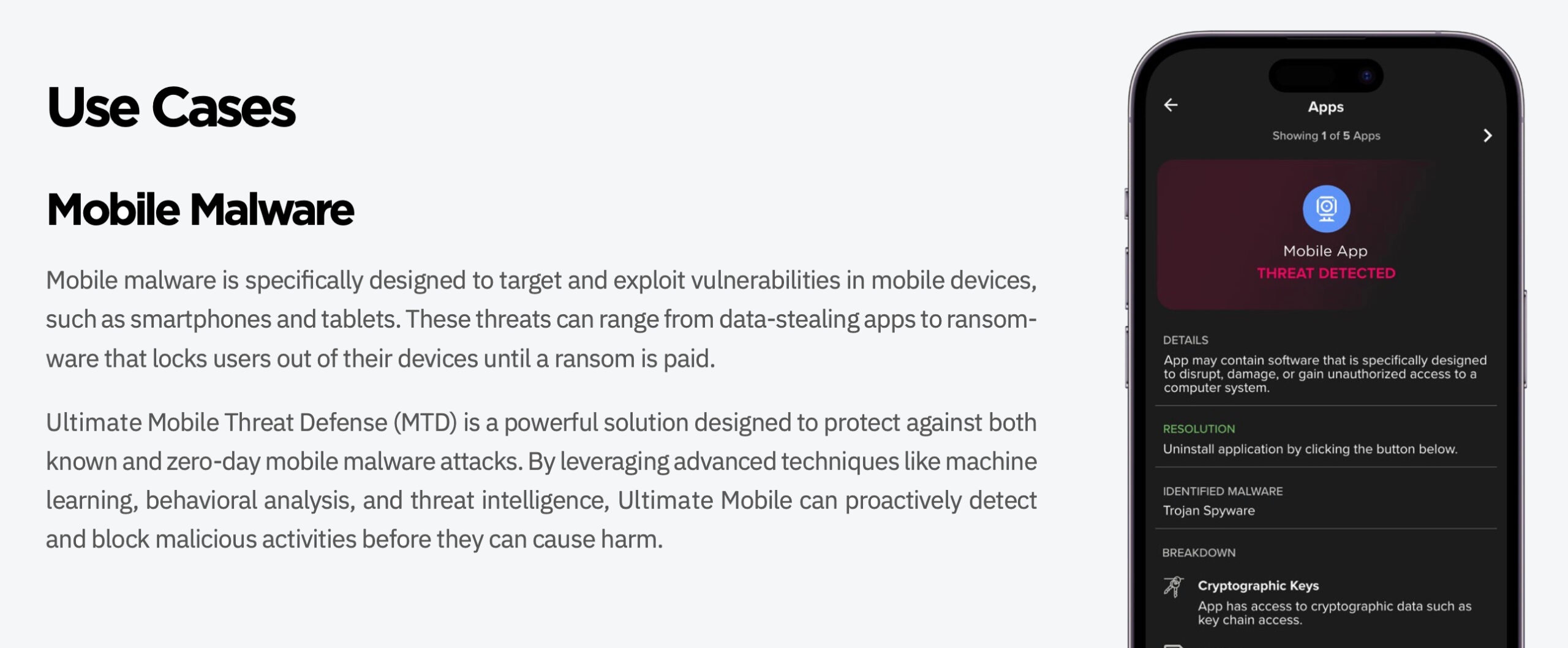
Mobile phishing targets mobile devices, such as smartphones and tablets, to deliver malicious content. Phishing has been around for some time, with adversaries using email messages and web pages as their primary method of attack. However, with the popularity of mobile devices and advent of AI-generated phishing tools and phishing-as-a-service (PaaS) providers, mobile phishing has become an increasingly common way for cybercriminals to access sensitive information. Types of mobile phishing include:
- Clickable links within applications: Attackers can embed malicious links within popular apps, social media platforms, or messaging services. Unsuspecting users who click on these links may be directed to fraudulent websites designed to steal their login credentials or personal information.
- Text message and SMS phishing (smishing): Smishing involves sending text messages containing deceptive content and links to malicious websites. These messages often appear to come from legitimate sources such as banks, government agencies, or well- known brands, enticing users to click on the link and enter their sensitive information.
Ultimate Mobile protects mobile users from phishing attacks, both from known phishing URLs and behaviorally identifies novel attacks. Ultimate Mobile alerts users to potentially dangerous links and SMS messages, preventing credential theft and more. Mobile credential theft remains a primary attack vector for mobile users, and Ultimate Mobile fills the void.
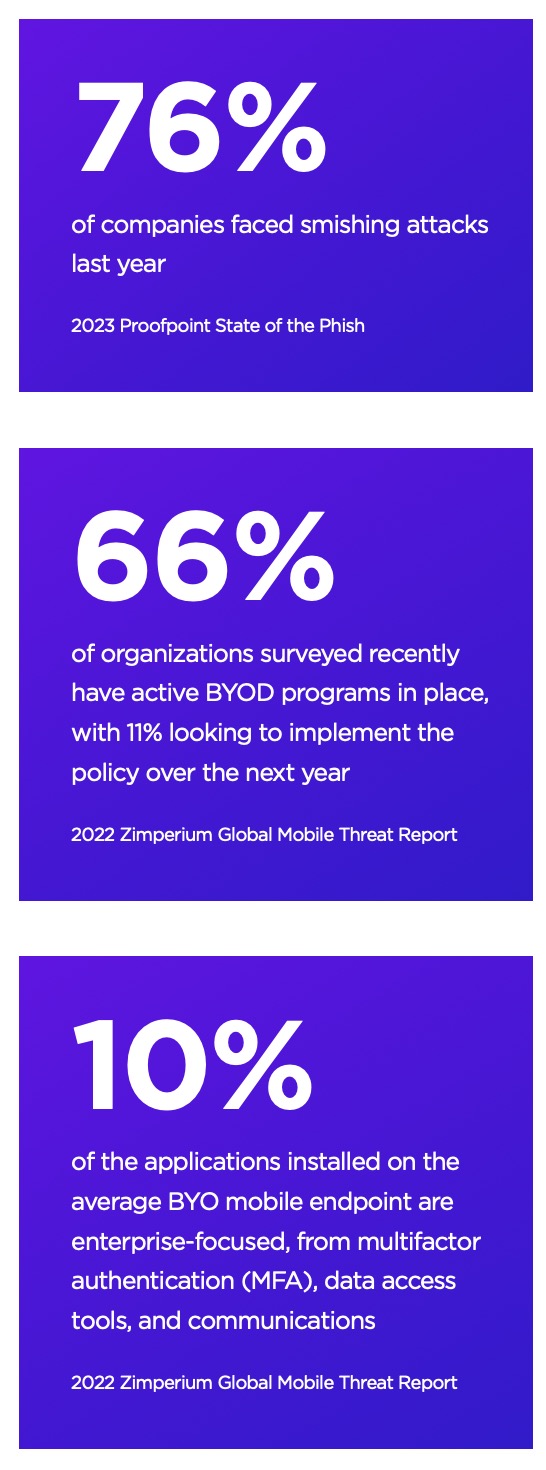
BYOD Security
Bring Your Own Device (BYOD) programs allow employees to use their own personal devices for work purposes. While this can increase productivity and reduce costs, it also presents a number of security challenges that must be addressed. As personal devices are often used to access sensitive company information, it is essential that organizations have measures in place to prevent unauthorized access or accidental data leakage.
Ultimate Mobile is a comprehensive MTD solution that offers optimal security for Bring-Your- Own-Device (BYOD) environments without compromising user privacy. Easily enroll BYOD devices without collecting browsing histories, passwords, local files, or personal data.