The Problem of Traditional Defense
Through the past two decades of tech booms, busts, and bubbles, hackers are still finding ways to breach security measures and desktops, laptops and servers have always been primary targets. The popularity of cloud and mobile computing has expanded the attack surface to the point that most enterprises deploy an expensive variety of overlapping software (antivirus, anti-malware, desktop firewalls, intrusion detection, vulnerability management, web filtering, anti-spam and more) on each of these endpoints to secure the organization.
But even with all of these solutions in place, high-profile companies are still being breached.
Why is traditional security not working?
The fundamental problem with traditional security is that they look for something known such as a known hash, IP address, vulnerability or behavior. Hackers respond by masking their attacks to bypass these traditional systems. It’s actually very easy to alter malicious code to bypass security measures. Anyone with basic coding skills can do it. When used together, these techniques can mask an attack creating a new, seemingly unknown attack that can bypass traditional security products.
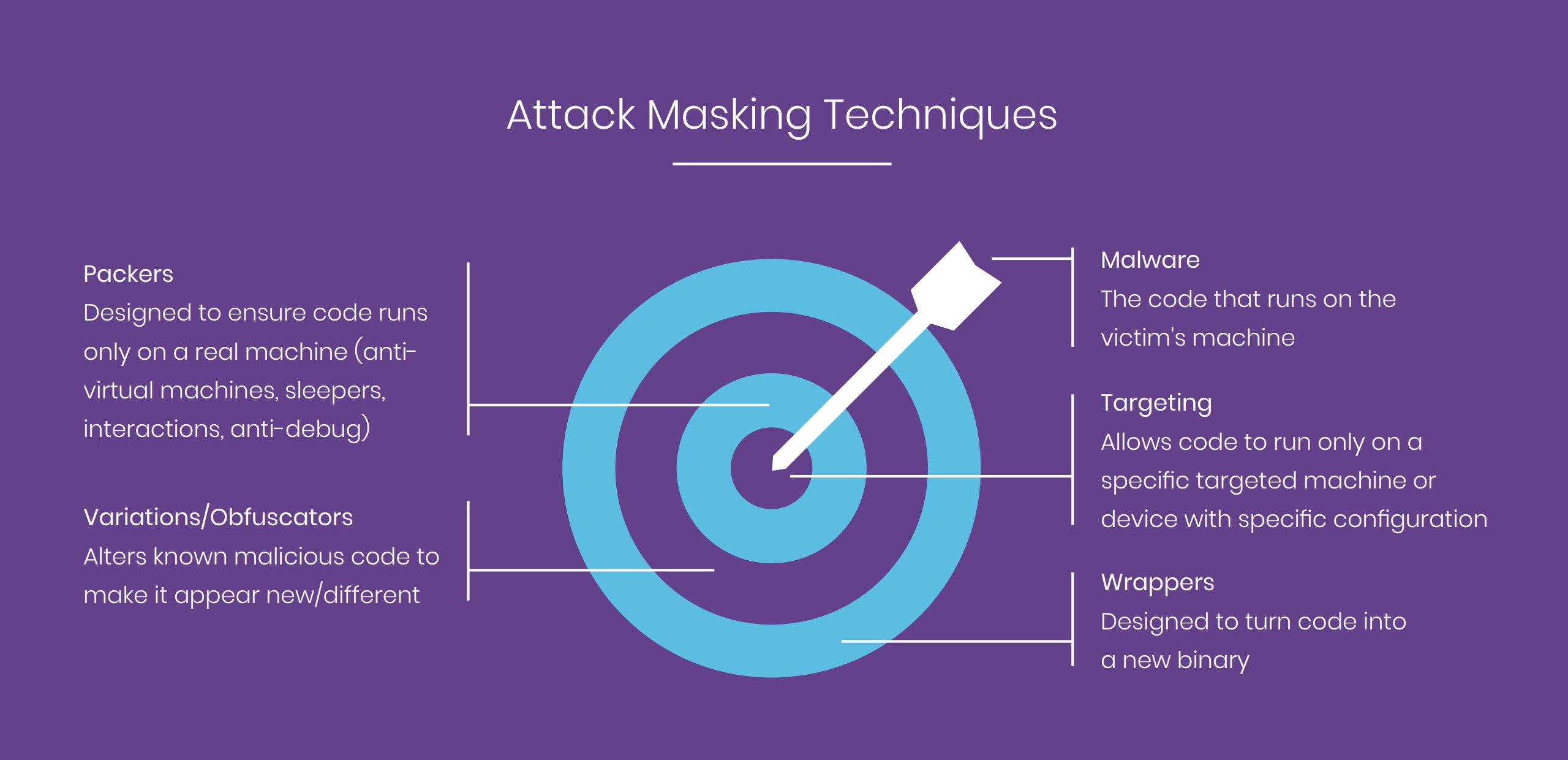
To make matters worse, hackers use different attack vectors (or paths) to deliver these attacks in unique, unpredictable ways. These techniques combined bypass traditional security solutions including antivirus and even next-generation anti-virus (NGAV) products.
A more modern defense approach
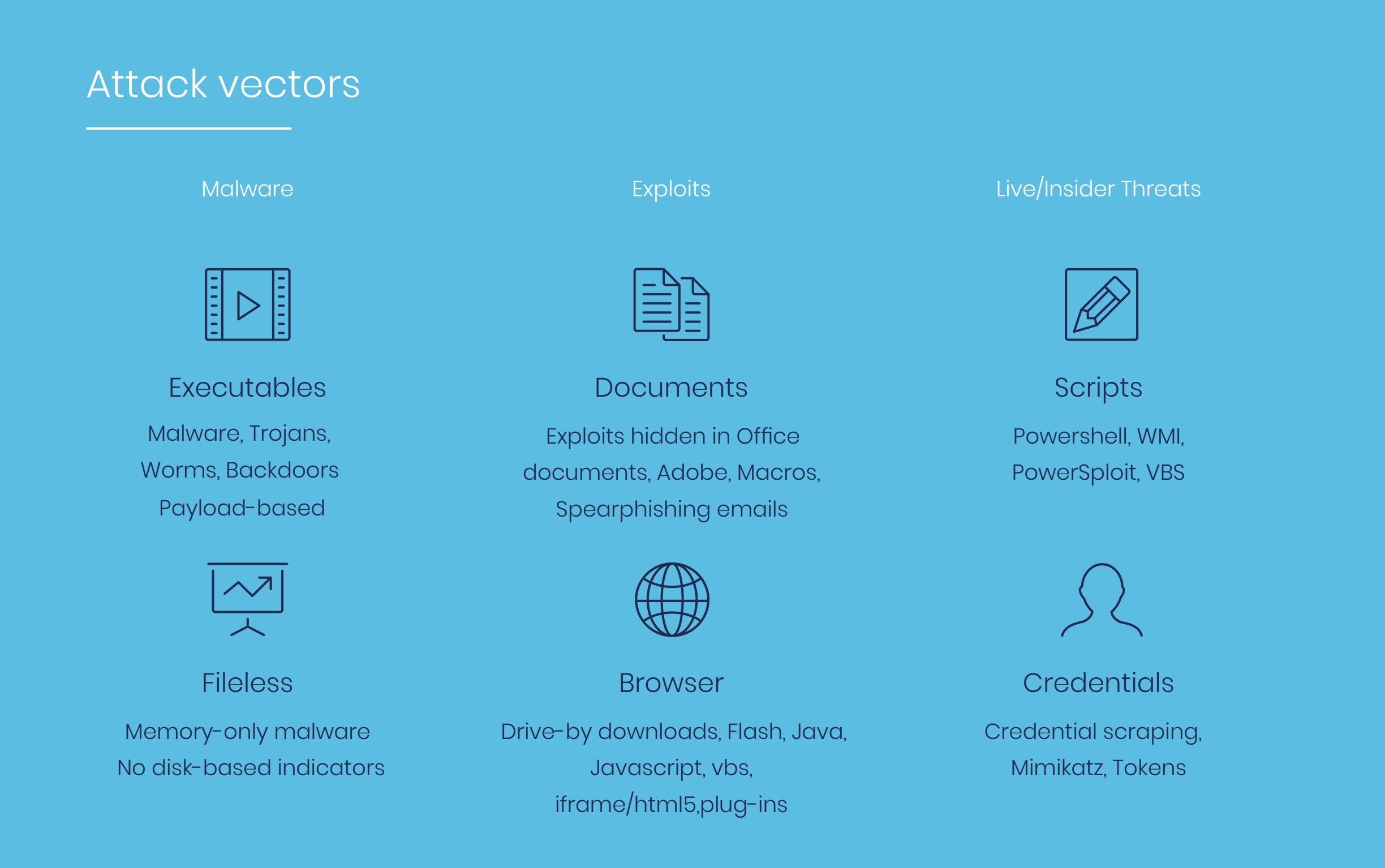
In recent years, a new type of technology emerged designed to detect and prevent threats at the endpoint using a unique behavior-based approach. Instead of simply scanning for signatures (or variants) of known threats with simple signature-based detection, next-generation endpoint security solutions must analyze file characteristics (to uncover known and unknown file-based malware) and also monitor the endpoint’s system behavior to identify suspicious, anomalous activity.
So what’s the best approach?
However, identification isn’t enough. A robust system must not only detect anomalous activity, it must offer both automated and manual responses and remediations to prevent malware and threats from spreading throughout the organization.
Going farther, the ultimate protection system must learn. As systems all over the world are attacked on a daily basis, the ideal system should correlate the data from those attacks and instantly make those signatures, and those complex and unique malicious behavior patterns known to all other deployed systems worldwide, instantly.
Put simply, if a new attack is seen on another system on another network on the other side of the planet, even if it’s not your system, you should receive an update to protect your systems, instantly. Ideally, this would require both advanced static and behavioral artificial intelligence (AI) analysis to correlate and extrapolate this data as quickly and efficiently as possible.
Since we seem to be in a dream space, let’s dream some more. Artificial intelligence can be extremely helpful. But there really is no replacement for a team of seasoned analysts to investigate the most bleeding-edge attacks and provide the support that only human experience can offer. When your systems are under attack, you want a team of experienced analysts working for you, not a lame chatbot frontend for an advanced AI. (In case you’re listening, we’re sorry, Siri!).
Based on all of this, what are the ideal expectations of an advanced endpoint defense system? Let’s run through the list.
Advanced malware detection
Your solution must be able to detect and block unknown malware and targeted attacks – even those that do not exhibit any static indicators. This involves dynamic behavior analysis — the real-time monitoring and analysis of application and process behavior based on low-level instrumentation of OS activities and operations, including memory, disk, registry, network and more.
Mitigation
Detecting threats is necessary, but alerts can go unresolved for days, weeks, or months, leaving malware running rampant in your systems. Automated and timely mitigation must be an integral part of your ideal solution. Mitigation options should be policy-based and flexible enough to cover a wide range of use cases, such as quarantining a file, killing a specific process, disconnecting the infected machine from the network, or even completely shutting the device down. Quick mitigation during inception stages of the attack lifecycle will minimize damage and speed remediation.
Remediation
During execution, malware often creates, modifies, or deletes files and registry settings and changes configuration settings. These changes, or remnants that are left behind, can cause system malfunction or instability. An ideal solution must be able to restore an endpoint to its pre-malware, trusted state, seamlessly while logging what changed and what was successfully remediated.
Forensics
Since no security technology claims to be 100% effective, the ideal solution must provide realtime endpoint forensics and visibility so that a seasoned remote analyst can quickly assess the scope of an attack and respond appropriately. This requires a clear, real-time audit trail of what happened on an endpoint during an attack and the ability to search for indicators of compromise.
Response Team support and incident analysis
An ideal solution would provide a team to review, respond to, document and escalate every threat, as needed. The ideal solution provides a hands-off experience for you, the client, escalating only the most urgent matters to you as needed.
Artificial Intelligence analysis
The ideal solution should provide an autonomous artificial intelligence-supported behavioral analysis engine that detects (and prevents) a wide variety of attacks, triggers protective mechanisms (kill, quarantine, remediate, etc) in real-time and continually sends and receives new attack data as needed, without consuming excessive resources on the client or network.
Vulnerability Management
In addition to monitoring active threats, the ideal solution must also proactively identify potential threats to the system by flagging applications installed on the endpoint that are known to be vulnerable to exploitation. The system should differentiate between safe and vulnerable versions of software, prioritize threats based on vulnerability and generate a mitigation report of all known vulnerable applications.
Cross-platform support
The ideal solution should protect a variety of endpoints (servers, workstations, virtualized and cloud devices, Kubernetes) running a variety of operating systems including Windows, Mac, Linux).
Mobile Support
No solution is complete without mobile device support. An ideal solution would provide protection, visibility, and response for mobiles and Chromebooks running iOS, Android and ChromeOS. Ideally it should protect against malicious links embedded within applications, protect from phishing, protect credentials from phishing and smishing (SMS) attacks and protect against mobile malware, including known and zero-day attacks.
Regular vulnerability assessments
While this ideal platform presents a strong reactive approach to a variety of attack vectors, there’s simply no substitute for regular vulnerability assessments in which a world-class team assesses your security posture from an internal and external perspective, probing each and every system for vulnerabilities that can be leveraged into compromise. This team would not only test for vulnerabilities, but present a clear, detailed remediation report guiding you step-by-step through the repairs and patches needed to remediate the threats, before they are exploited. In a perfect world, this team would also offer remediation support, performing the repairs for you.
The Ultimate Defense Platform
When combined, these approaches provide a world-class defense solution that will drastically improve your security posture, instill confidence in your clients and investors, and above all else, drastically reduce your risk for compromise and catastrophic loss of data. In fact, this combined solution is exactly what large-scale enterprises around the world strive to accomplish with teams of full-time, well-trained, experienced experts.
The statistics support the need for this level of protection. A recent study reveals that nearly 43% of cyber-attacks target smaller organizations and projects yet only 14% of these organizations deflected them. Nearly half of business targeted by ransomware pay the extortion fee. 55% of ransomware hit businesses with fewer than 100 employees, and 82% of ransomware attacks were targeted at companies with less than 1000 employees. A staggering 75% of attacks targeted companies making less than $50 million in revenue. As of June 2023, small businesses spend between $826 and $653,587 on cybersecurity incidents, and 42% of companies are experiencing cyber fatigue or a sense of apathy toward proactively defending against digital attacks.
Although the statistics show that your organization will be targeted, through our decades of experience, we’ve come to realize that this level of protection is well beyond the financial means of smaller organizations, and it is for just this reason that attackers have turned their attention to these less-protected (yet lucrative) targets.
We hate this, and we’re determined to do something about it. That’s why we are offering the Ultimate Defense Platform, with all of the above features to smaller organizations at a reasonable cost that fits well within the budget of even the smallest SMB.
If you’ve read this far, you might be wondering how we can possibly provide this level of protection at a reasonable cost. The secret is quite simple. We partner with the best-in-breed software solutions providers and purchase large licenses of world-class software, significantly reducing the cost per endpoint. As security professionals we pick and choose our solutions carefully, buying the best-in-class software for each and every need without succumbing to the sales pressures of vendors that simply want us to buy all their stuff, ignoring better-suited competitor products.
We configure these complex software products to work together seamlessly. We update, configure, maintain and monitor them so you don’t have to. When an incident occurs, our team makes sure that every threat is reviewed, acted upon, documented, and escalated as needed. In most cases we interpret and resolve threats in about twenty minutes and only contact you for urgent matters.
And although there are many moving parts to this ultimate solution, your part in this is quite simple. You’ll simply install a single software agent on each of your endpoints and we’ll do the rest. If you want to be hands-off, simply leave it to us and we’ll only contact you if we detect something that requires your assistance. If a vulnerability scan requires remediation, our team can install the fixes.
On the other hand, if you want to get hands-on, we’ll provide access to a centralized console that allows you to get as involved as you would like to be. You can configure, tweak, monitor and respond to alerts as you see fit. We’ll still be there when you need us, but we offer flexibility for your specific level of need.
The bottom line is that we’re fed up with watching small organizations take such a significant hit, year after year, and we’ve dedicated ourselves to doing something about it. Thanks for taking the time to read about our approach as we’ve developed this Ultimate Defense Platform. We’re excited about the prospect of partnering with you in the fight against cyber crime!
We’re available to chat with you and answer any questions you might have. Please don’t hesitate to reach out!